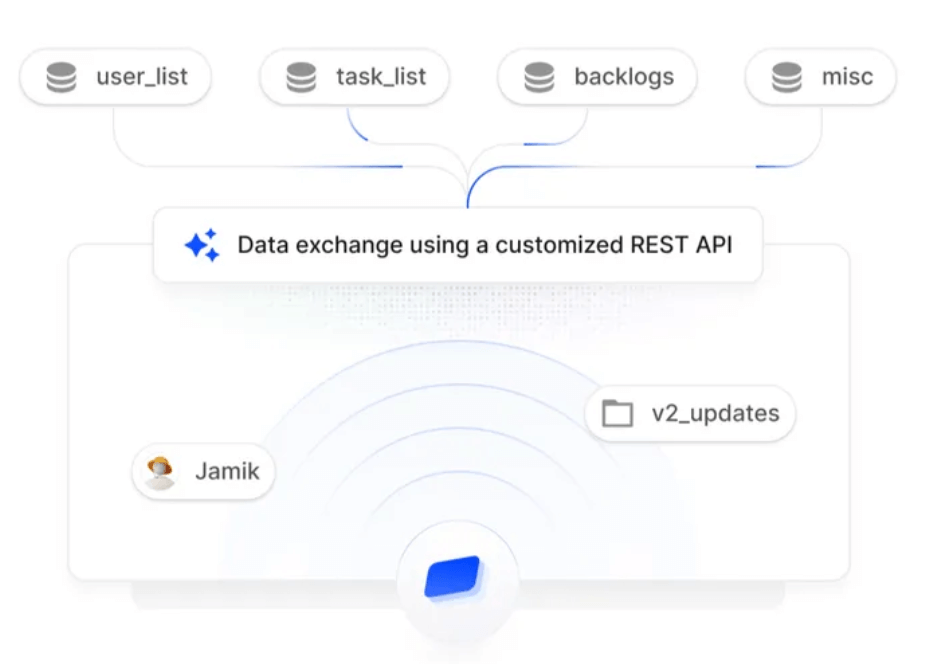
Improper access configurations are a major cloud risk. We audit and optimize IAM policies, roles, and service accounts to enforce least-privilege access. Control who can access what—securely and transparently.
Misconfigured storage buckets, open ports, or public resources can lead to costly exposure. We scan your environment using Security Command Center and custom rules to uncover vulnerabilities. Fix issues before they’re exploited.
We align your setup with Google’s security frameworks, including workload identity, VPC Service Controls, and data encryption standards. Build a resilient and compliant security posture from the ground up.
Threats evolve fast—your defenses should too. We integrate tools like Chronicle, Cloud Audit Logs, and Security Command Center Premium for continuous monitoring and automated alerting. Stay ahead of threats with intelligent cloud defense.
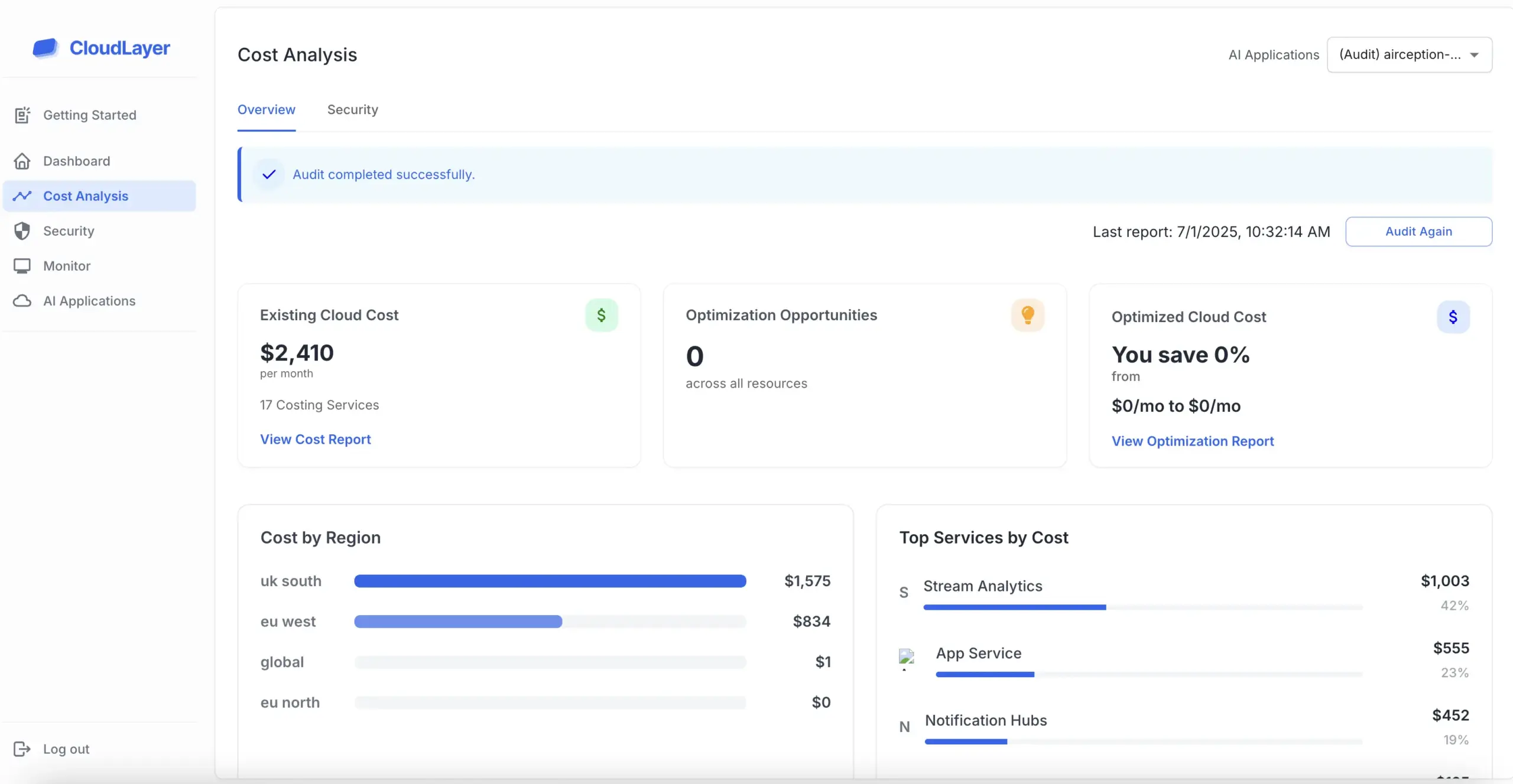
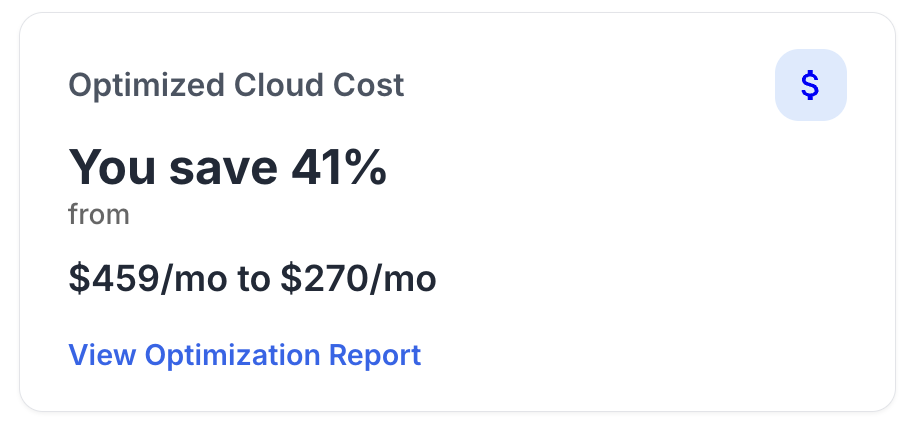
Start using CloudLayer and experience a new level of efficiency.